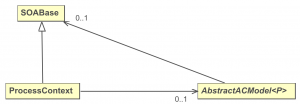
Some components in SEWOL, like access control models, use SOABases, which contain lists of possible activities, subjects, and objects. In the access control models in section 2 it has been used implicitly. SEWOL defines a ProcessContext, which supplements the SOABase class by an access control model and a mapping of data usage modes for specified objects in an activity. This way permissions of subjects to execute and process activities to use objects with specified usage mode can be defined. Figure 3 shows the relation of SOA base, process context, and access control model.
A process context based on an existing SOA base can be built using the following code snippet. As underlying access control model the formerly defined RBAC model is used.
ProcessContext context = new ProcessContext(base);
context.setACModel(rbac);
context.setDataUsageFor("act_1", "obj_1", DataUsage.WRITE);
context.setDataUsageFor("act_1", "obj_3", DataUsage.READ,DataUsage.CREATE);
context.setDataUsageFor("act_2", "obj_1", DataUsage.WRITE);
context.setDataUsageFor("act_2", "obj_3", DataUsage.READ,DataUsage.CREATE);
context.setDataUsageFor("act_3", "obj_2", DataUsage.DELETE);
System.out.println(context);
The corresponding output is the following:
Context{
name: base
activities: [act_2, act_1, act_3]
subjects: [sub_2, sub_1, sub_3]
objects: [obj_3, obj_2, obj_1]
activity data usage:
act_2: {obj_3=[CREATE, READ], obj_1=[WRITE]}
act_1: {obj_3=[CREATE, READ], obj_1=[WRITE]}
act_3: {obj_2=[DELETE]}
activity permissions:
act_2: [sub_1, sub_3]
act_1: [sub_1, sub_3]
act_3: [sub_2, sub_1, sub_3]
object permissions: obj_3: [sub_2[] sub_1[CREATE, READ] sub_3[CREATE, READ] ] obj_2: [sub_2[DELETE] sub_1[DELETE] sub_3[DELETE] ] obj_1: [sub_2[] sub_1[WRITE] sub_3[WRITE] ] execution authorization: act_2: [sub_1, sub_3] act_1: [sub_1, sub_3] act_3: [sub_2, sub_1, sub_3] }
At the beginning of the output the SOA base with the possible subjects, objects, and activities is shown. Under the heading activity data usage, the data usage modes of process activities are listed. The following headings activity permissions, object permissions, and execution authorization represent the underlying access control model, where the execution authorization depends on activity and object permissions. Subjects who are authorized to execute an activity also need permission to access data objects in the way the activity does.
To conveniently edit process contexts, SEWOL comes with a corresponding Java Swing dialogue. It can be created using the following command:
ProcessContextDialog.showDialog(null, context);
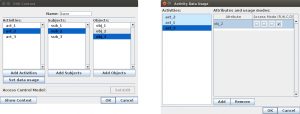
(4a) Dialogue for editing a SOA base.
(4b) Dialogue for assigning data usage modes to activities.
Figure 4: Dialogue for editing process contexts in SEWOL.
The resulting dialogue can be seen in Figure 4a, where the underlying SOA base can be edited. By selecting the button Set data usage, a new window opens (see Figure 4b), where data usage modes can be assigned to objects for activities.
- (4a) Dialogue for editing a SOA base.
-
- (4b) Dialogue for assigning data usage modes to activities.
Figure 4: Dialogue for editing process contexts in SEWOL.
- (4b) Dialogue for assigning data usage modes to activities.