The simulation method, depicted in Fig. 1, takes a series of business process specifications as input and generates a process log that contains traces of these specifications. Based upon the security and compliance requirements, deviations from the defined control flow are generated with the help of transformers which encode specific trace properties that are either enforced or violated on a random basis. Together with the ability to subsequently generate traces of a series of different business process models into a single log, the approach provides for a definition of an attacker model, which can be configured in a detailed way for a particular test case. Generated logs are outputted in MXML (a format for process mining), as well as plain text.
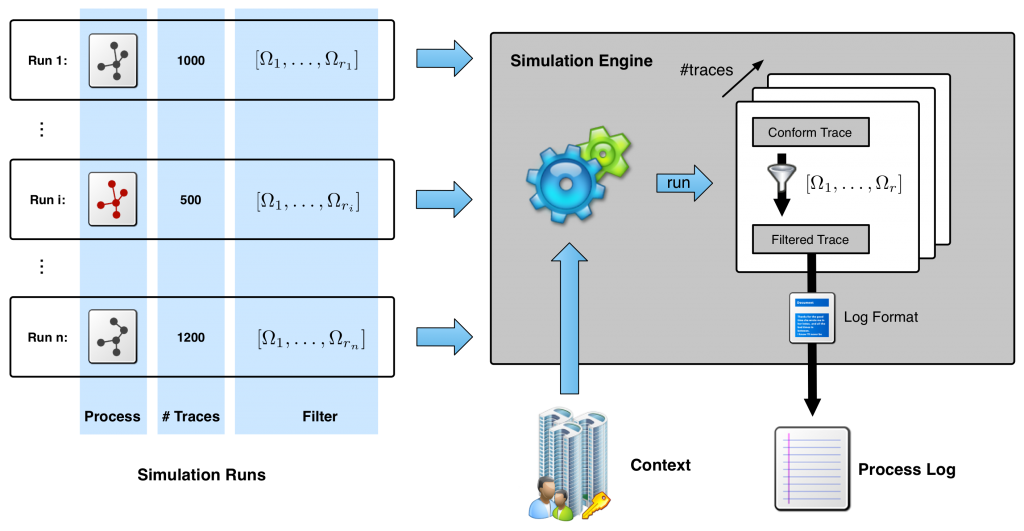
Processes subject to simulation are considered to be executed within a context. While the control flow of a process defines possible execution traces, subjects authorized to execute process activities and objects used by activities are defined by contexts. Our approach allows to define simulation runs, each relating to one process model which is processed one after another according to the number of desired traces for each run. This way, the engine is capable of simulating situations in which there isan initial model for planned process behavior, but a variant of this model was executed for some time, possibly due to the activity of an attacker or process variation/flexibility. To support the user in defining such variants, we define model transformation operators that replace specific control flow patterns of a process. Additionally, each simulation run can relate to a set of trace transformers which operate on trace level.
During the processing of a simulation run, the engine generates valid log traces according to the control flow of the corresponding process and context and then passes them through the trace transformers which apply transformations in a post-processing manner. Trace transformers can remove or add process activities (simulating skipped activities or incomplete logging), as well as change information within traces in a way business related properties like separation/binding of duties or authorization constraints are enforced or violated.