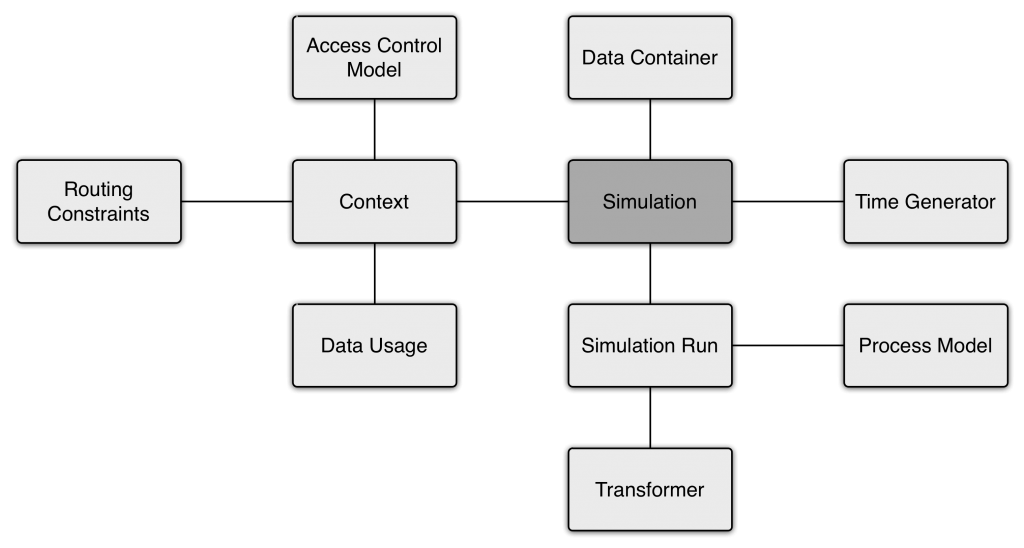
Simulation Components
The event log synthesis approach presented in the conceptual section has been implemented as a standalone Java application called SecSy (Security-oriented Log Synthesis). The tool allows for flexible configuration of all required parameters and the creation and editing of corresponding synthesis components.
The time generator component contains all timing related simulation properties, including the start time for the simulation (date for first trace), the number of cases per day, office-days and -hours, as well as individual activity durations and delays between succeeding activities. All properties can be randomized by adding deviation bounds. The possibility to add several simulation runs is useful for simulating the execution of different process models or different property enforcements along time. To model the requirements that should (not) hold for single simulation runs (thereby specifying the policy applicable to the process), the user can assign different transformer configurations. This way, the frequency and kind of security violations can be thoroughly configured. In the case of simulation type DETAILED, the user has to specify a context and a data container. Data containers generate values for data items used during process execution (e.g. credit amount) and store the values until a trace is completed. This way, the consistent usage of attribute values along a complete trace is ensured. A context holds subjects and their permissions to execute activities and access data elements in form of an access control model together with activity data usage (attributes used by activities) information. To specify subject permissions, the user can choose between an access control list or a role based concept, which is particularly helpful for large contexts. Additionally, a context allows to specify constraints on attribute values that can be added to process activities. This influences the generation of process traces in a sense, that only those activities are executed whose constraints are fulfilled. On Petri net level (which is the used meta-model for process models), the set of enabled transitions is reduced according to existing constraints, when the simulation tool decides about the next transition to fire.
Installing SecSy
SecSy is hosted as a SourceForge-project and can be downloaded from http://sourceforge.net/projects/secsy/. The tool requires a Java VM on the target platform.